information-security-resources
- Cylance Endpoint Protection
- Cybersecurity Awareness
- Microsoft Advanced Threat Protection
- SANS Security Program
- Forward Email as an Attachment
- Additional Resources
All antivirus products on University-owned computers are being replaced with Cylance Endpoint Protection in order to enhance our ability to predict and protect our University from cyberattacks.
- On Windows computers, we remotely disabled Microsoft Defender and installed Cylance. This will occur silently (without prompts) and no user interaction is required. When the installation completes, you will notice a small green Cylance icon in the system tray.
- The installation of Cylance on Macintosh computers will require user interaction. When Cylance is pushed to Macs remotely, it will uninstall ESET and users running macOS 10.13 or higher will receive prompts to finalize the installation. Please follow these instructions for additional information (authentication required).
- These changes were gradually implemented on Staff machines on January 14, 2021 and Faculty machines on May 25, 2021.
October is Cybersecurity Awareness Month, a national program to help create awareness of the many ongoing threats we face whenever we are online.
The Division of Information Technology is bringing this initiative to our campus, as online security is an essential shared responsibility that concerns us all.
In October we will be sharing important security resources with you through weekly emails. We will also be answering your questions regarding working securely from home at our Virtual Cybersecurity Forum.
Virtual Cybersecurity Forum
Please join IT Security on Thursday, October 29 at 10:00 a.m. for a short discussion on staying secure while working remotely. We will be providing you with tips and best practices on how to stay secure when working remotely, and will answer your questions. Zoom link for the event will be emailed to registrants the day before the event.
Register today! You can also submit your questions in advance with your registration.
Cybersecurity Videos (2020)
The Information Technology Division is planning to gradually deploy ATP to the University starting in April 2020.
Due to the recent increase in email attacks from bad actors taking advantage of the COVIC-19 crisis, we have decided that it is crucial that we continue the implementation of ATP to provide our University with increased protection.
What is ATP?
Microsoft’s Advanced Threat Protection provides additional protection from email-based malware attacks by evaluating links and attachments in emails and blocking them if deemed malicious. ATP uses the following strategies to protect your email:
- Safe Links: evaluates and confirms the validity of links in emails.
- Safe Attachments: scans and protects against harmful email attachments.
- Messages that are deemed unsafe by ATP standards will be redirected to your Junk folder.
Safe Links
Safe Links evaluates every link in an email in real time to determine whether the link is safe. All links evaluated by Safe Links will be replaced by a longer URL that that begins with https://na01.safelinks.protection.outlook.com/? , similar to the example shown below.

If you click on a malicious link in an email, a warning will be displayed instead of the actual website.
Safe Attachments
In addition to the virus scanning, Safe Attachments analyzes every attachment to detect malicious content. If malicious content is found, it will result in:
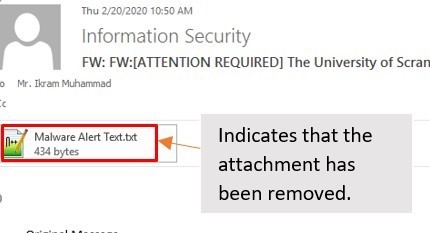
- Attachment Removal: you will still be able to read the email, but the attachment will have been removed (see sample below).
- Quarantine: The email message will be removed and placed in quarantine for 30 days.
FAQ
If I mouse-over a link from a trusted source, why does it look like a weird address?
Hovering your mouse over hidden links is always a good practice, and can continue to serve you well even with ATP enabled. The Safe Links address indicates that it has been scanned for malicious content. Safe Links can be forwarded, as recipients will be able to access the content.
Can I opt out?
No - it is paramount that all University Office 365 emails are scanned and protected.
I received an email with an attachment but it just says, “ATP Scan In Progress – Outlook Item” instead of the file I was expecting. Why?
As each message comes in to Office 365, it is scanned for dangerous attachments. The message body can be read while that scan is in progress, but the attachments cannot because they aren't yet thought to be safe. While the attachment scan is ongoing–typically less than two minutes–you'll see a placeholder in the attachments area. Close then re-open the message to see if the scan is complete and the attachment is available. Note that even if you read the body of the email before the scan completed, following the scan, the message status will reset to unread.
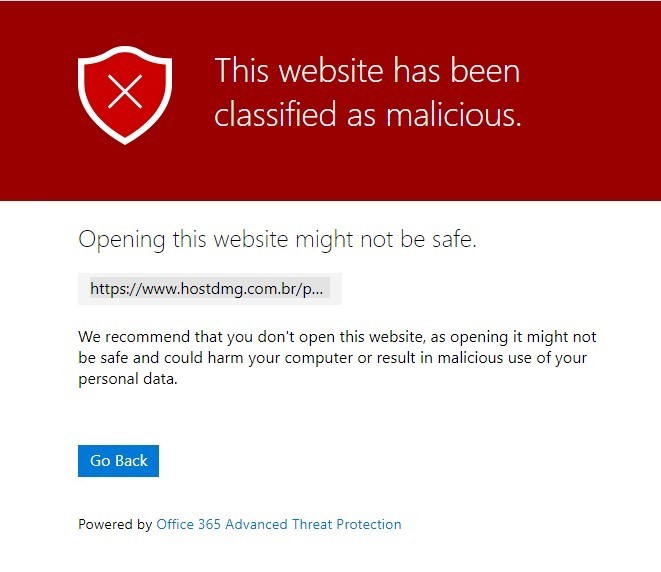
I clicked on a link in my email and it told me, “This website has been classified as malicious.” Why?
If a link in your message points to a location that has been verified to be malicious in some way, Safe Links will stop you from accessing that location when you click on the link. If you think a site has been blocked by mistake, please report it to infosec@scranton.edu by forwarding the message as an attachment.
How does this impact my file storage?
ATP also provides protection against opening or downloading of files from SharePoint and OneDrive. When accessing a file from these locations, it will be scanned and if found to be malicious it will be blocked from opening or downloading. Although the blocked file is still listed in the document library and web, mobile, or desktop applications, the blocked file cannot be opened, copied, moved, or shared. People can, however, delete a blocked file.


The SANS Security Awareness Training is comprised of a set of short videos that helps build awareness of the online threats we face. IT Services has registered all full-time personnel at the University into the SANS program.
All staff and faculty are encouraged to take the SANS Computer Security video training, even if you have taken it before. New videos have been added. This important training will assist all computer users on campus to understand how we, as individuals, can be the target of identity thieves or other malicious actors. The videos are short, usually 3 or 4 minutes in length. Instructions for the SANS Security Awareness site, log in, and other information will be emailed to all members of the University community.
Need account help? Your username is your firstname.lastname@scranton.edu. If you don't know your password, you can reset it by clicking the Forgot your Password link on the SANS Training Center website.
- Select the email you want to forward, then go to the Home tab.
- In the Respond group, select More Respond Actions.
- Select Forward as Attachment.
- In the To text box, enter the email address of the recipient.
- Select Send.





